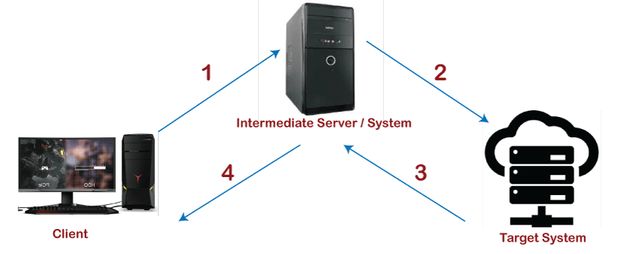
What is Cybersecurity? Cybersecurity is a practice of protecting the systems, networks from digital attacks. Now that many of the companies, financial sectors, government organizations are looking forward to protecting their data from hackers or cybercriminals . These attacks must be handled by engineers, pen testers, security testers and other professionals to prevent the attack. Why Cybersecurity is important? Cybersecurity is important across different sectors such as government organizations, startups, mid and large enterprises and even for personal use. But why do think security is very important? Gone are the days of simple firewalls and antivirus software being your sole security measures. Cyber threats can come at any level of your organization So, educating your employees about simple scams like phishing, ransomware attacks or other malware designed to steal intellectual property or personal data. Cybersecurity risk is increasing and withou...